Ransomware wants your data and your money. If you own a small to mid-sized business and still think bigger companies are better targets, you might want to think again.
Ransomware has become our modern day Bonnie & Clyde.
Simply put, ransomware comes from criminals creating malicious software designed to block access to your computer systems and data until you pay them a sum of money. It has become a very lucrative business.
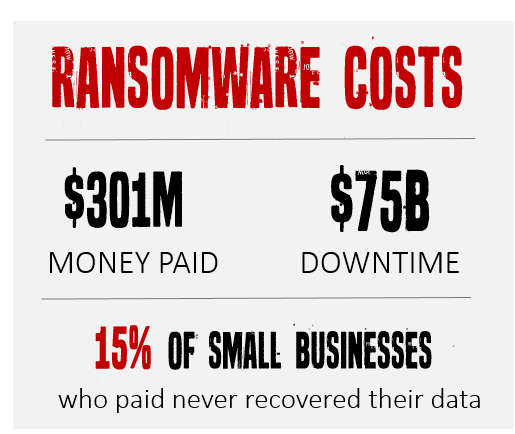
In the last 12 months, $301 million dollars have been paid by small businesses, just like yours, to ransomware thieves.
This service allows thousands of criminals to release a relentless number of attacks and push new versions of malware on demand. They march right into your business through your computers, mobile devices, network connections and your employees looking for any vulnerability.
Ransomware attacks grew from 4 million in 2015 to 638 million in 2016 based largely on RaaS (ransomware as a service).
Once they access and lock your data, they hold it for ransom.
On average, they get between $500 and $2000 dollars of your hard earned money along with days of business downtime. They usually request payment within 24 hours in the form of bitcoin. Bitcoin makes it very difficult for them to be caught. Is that why the price of bitcoin keeps rising?
It’s not easy for the average small to mid-sized business to protect themselves, but here are 7 deadly sins to avoid when it comes to ransomware.
1. Ignore the Whole Cyber Issue
Let’s face it. Reading about cybersecurity is not all that fun or interesting for most of us. Neither is trying to figure it out. However, ignoring it is the worst thing you can do.
Ransomware has become big business. These thieves are looking for easy targets and you are it. In face, they love hitting up vulnerable businesses multiple times. Criminals are using their ransom money profits to innovate new ways into your business.
They have the methods to hit thousands of businesses day and night. It’s not personal. Below is the effect of ransomware on small businesses from Q3 2016 to Q2 2017.
2. Partial or No Backup & Recovery Strategy
According to the US Department of Homeland Security, the #1 solution for ransomware protection is a solid backup and disaster recovery plan.
Because ransomware is constantly changing, even the best security software can be hacked. This is why your last and most critical layer of defense is backup and recovery.
Too many businesses think they have backup covered only to find out too late that they dont.
The simplest way to test your business protection is to have network security professionals perform vulnerability scans and identify problem areas.
3. Failure to Keep Devices & Systems Updated
Software, browsers, operating systems, etc. can all be security risks. Yes, they can also be annoying, which is why many businesses and people avoid them.
Software upgrades and patches are released regularly now to block known threats as they become available.
The Experian data breach was a good lesson for this. Experian did not apply a critical patch to all hardware and software it needed to and that’s how the cybercriminals got into the system.
In other words, don’t listen to bad advice like stop Windows 10 from making automatic updates. You should always update.
This is a screen you never want to see.
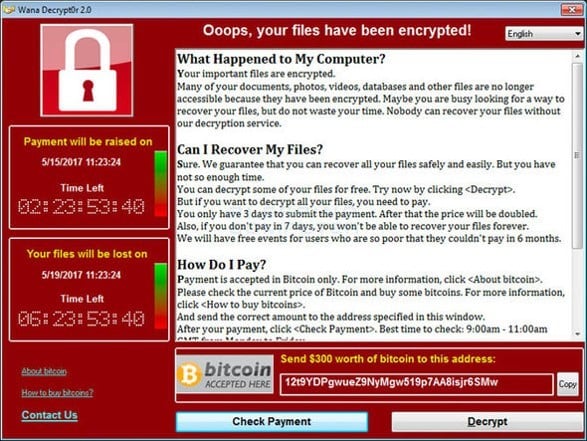
4. Little or No Endpoint Protection/Antivirus
Endpoint devices are any device that can connect to the Internet. This includes laptops, smartphones, tablets and a whole host of appliances like security cameras or monitoring devices that are Internet enabled.
These are often an easier starting point to gain access to your business and usually the most vulnerable.
Don’t skimp here. Having strong anti-virus and malware software for these devices is a critical security step for any business and no, free software isn’t going to cut it.
5. NOT having a next generation firewall
Firewalls come in all shapes and sizes and sit between you and the internet. Maintaining an old firewall that doesn’t keep up with today’s threats is like begging to be hacked.
All businesses today should have modern security appliances that get updates from the cloud. At a minimum, you need one with intrusion prevention rules, filtering and updated advanced malware protection to keep your business running.
Today, most of us should also consider adding a firewall to our home networks.
6. LACK of security awareness by employees
90% of ransomware makes it into your company through your employees. The methods have become so sophisticated that even security professionals have a hard time spotting them.
Today, a ransomware thief can actually make an email look like it’s coming from HR, IT personnel or the CEO. Training your people about social engineering, phishing schemes or dangerous links is criticial in today’s business.
7. Thinking that anyone can do security
The CIA now considers cyberthreats to be a way of life. When there is money to be made, criminals will find a way. Cybersecurity implementation is just as important as locking your business doors.
As our businesses become more digital, it is growing more complex. The more devices we use, the more data we rely on, share and access from anywhere, the more we need to protect.
These criminals don’t take naps and the list of items your business needs to protect from these cyber thieves just keeps growing. It’s important for you to have and manage security for your business that gives you the maximum amount of protection without breaking the bank.
Small businesses have been turing to professionals to help them manage the security in cost-effective ways.
Balancing between security risk and the likelihood of occurrence is the most important ingredient to make sure your money, reputation and productivity stay intact.
What cybersecurity solution does your business really need?
A layered approach to security is important and serves as the best way to combat today’s would be criminals. One that keeps your data assets, business continutity and any compliance needed in mind.
The first and best step is getting a Security Assessment.
{{cta(‘4958c19f-2a59-48f2-b1ab-0bcda0b5b868’)}}
